
The Standard for Digital Certainty.
Immutable Chain of Custody. Zero-Knowledge Encryption.
Use CryptoLock™ to encrypt your personal photos, journals, and documents with military-grade AES-256. Your keys never leave your device. Total privacy, zero cost.
Use ProofLock™ to mathematically notarize your media on the public blockchain. Prove exactly what happened and when it happened, immune to AI alteration.
Beyond encryption. ProofLock creates Self-Verifying Containers. Send files that prove their own integrity and origin the moment they are opened.
Powered by Ghost-Link™
We decouple Identity from Content. Unlike traditional encryption, our architecture allows you to share verified, tamper-proof assets without ever exposing your master private identity.
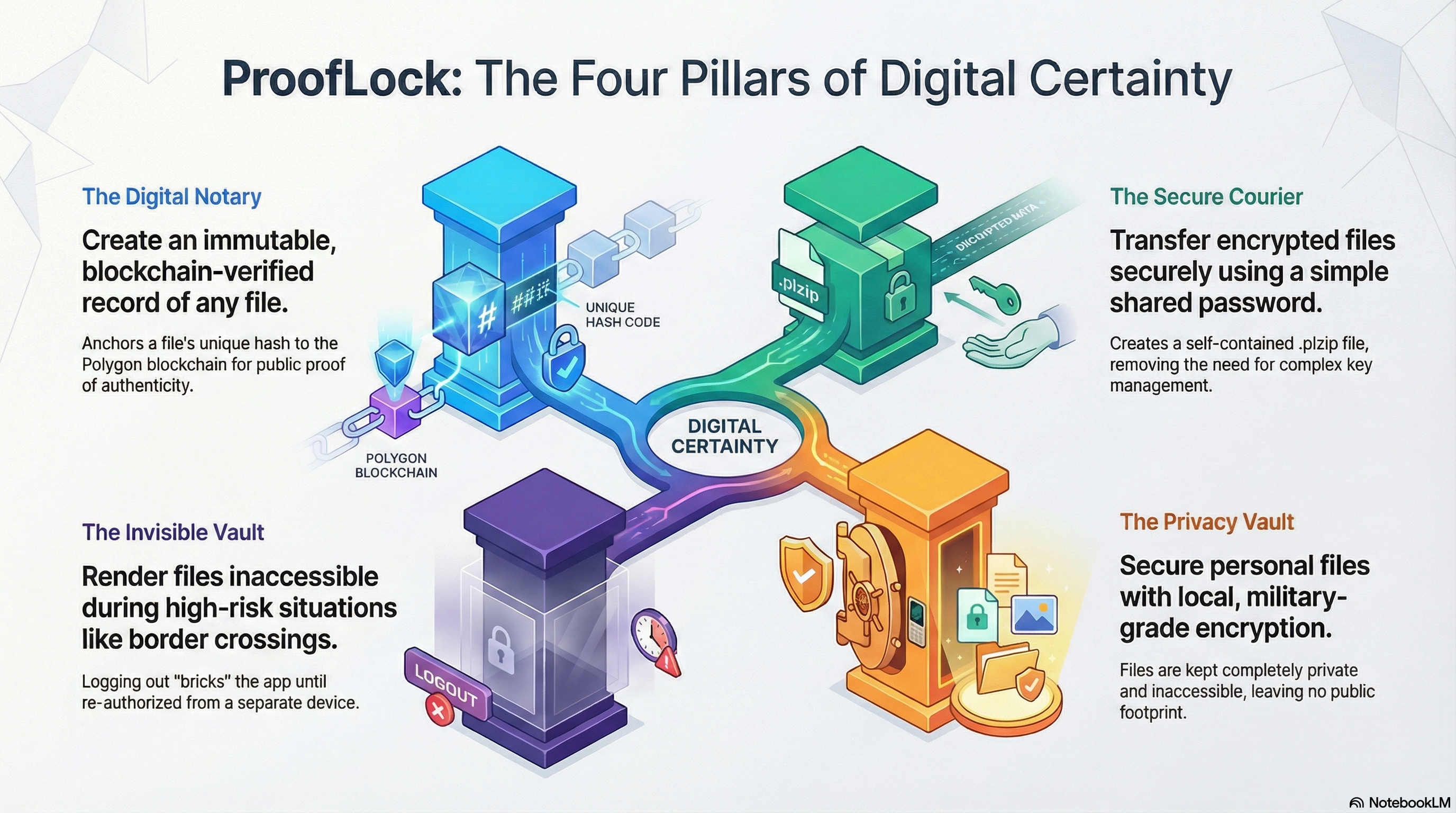
How ProofLock Works
The Privacy Vault
Keep your secrets secret.
- Select any file (Photo, Video, Doc).
- Tap CryptoLock (Grey Button).
- Your file is encrypted locally with AES-256. No cloud backups. No AI scanning. Only you hold the key.

The Digital Notary
Prove it is real. Forever.
- Select your evidence (Contract, Scoop, Accident Video).
- Tap ProofLock (Green Button).
- We generate a unique digital fingerprint and anchor it to the public blockchain. You now have mathematical proof of existence.
Authenticated Transport
The Pipe doesn't matter. The Package does.
- Traditional tools secure the transfer. We secure the asset.
- Wrap & Verify: The recipient automatically verifies the blockchain signature upon decryption.
- Total Assurance: Mathematical proof that the file received is 100% identical to the file sent.

The Invisible Vault
Air-Gapped Security.
- Entering a high-risk zone? Tap Log Out.
- This destroys the decryption keys in your phone's Secure Enclave.
- Your vault becomes mathematically inaccessible until you re-authorize via a separate device.

A 30-year veteran of Enterprise Security and Data Integrity, Paul engineered ProofLock to solve a critical flaw in modern digital media: The lack of verifiable truth.
"In a world where AI can fabricate reality, we need a mathematical shield to protect our history. ProofLock isn't just an app; it is the standard for Digital Certainty."